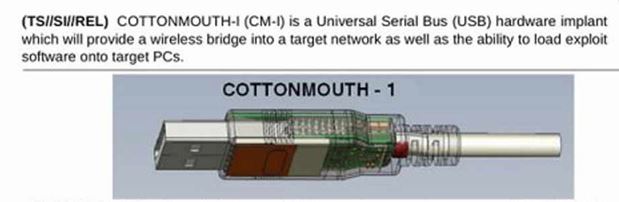
In late 2013 a leaked NSA document was published by the press. The document originated in the 2008-2009 timeframe and it contains 49 pages of NSA hardware and software exploits.
It contains software exploits for all major commercial routers, surveillance devices, and hardware and software exploits for phones and personal computers. While most of the specific phones and operating systems from that time period have been retired, it is still useful to analyze the categories and behaviors of these exploits.
I would recommend that all targeted individuals review this document and save it to their research folder.
Notable entries include COTTONMOUTH, which is a usb or ethernet cable which can deliver malware, and includes a wireless RF transmitter with its own over the air protocol. Another notable entry is NIGHTSTAND which is a briefcase sized transmitter able to wirelessly exploit a PC located up to 8 miles away.
I think the main take-away for targeted individuals would be to 1) understand what types of attacks are possible, 2) recognize that attacks are both hardware and software based, and 3) many attacks are going over their own network, and not your home network.
References:
ANT catalog. (2023, April 7). Wikipedia. https://en.wikipedia.org/wiki/ANT_catalog
Follow @TargetedTechTlk